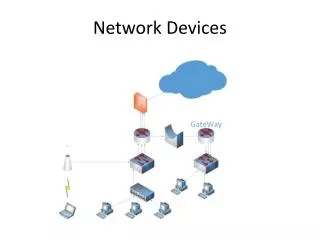
11 Creative Ways to Write About cookie banner gdpr
For intricate systems like SAP, it's often preferred to utilize devices created specifically to examine and also examine SoD disputes and also other selections of system task. The sensible safety devices employed for remote gain access to must be fairly rigorous. How to scan the entire Internet The computer system software was produced really with the whole Net, although it is additionally rather valuable for smaller, internal networks. The templates may have a broad selection of target markets. They can be used to produce a few of one of the most effective audit plans. A Double-Edged Sword The concept of a system audit might become politically undesirable. Service continuity program can substantially lessen your loses if ever before you're hit by the catastrophe. A federal government can accumulate your individual details. All policies are offered in MS Word format and can be conveniently customized according to your demands. The plans might be made use of by any type of covered entity. Therefore it will certainly end up being vital to have a considerable and also plainly verbalized plan in position which might aid the company members to understand the importance of personal privacy as well as security. For example, the current GDPR plan modification is an essential part of compliance. Often, whenever there isn't any proper framework in place and also obligations aren't plainly defined, there's a high risk of a violation. Your organization has a lot of cybersecurity plans in place. The sort of strategy a company is dependent on many elements, for example, dimension of the company, the employer's dedication to supplying benefits, the organization's objectives and objectives, the expenditures of keeping the strategy, and so on. Little as well as massive organizations may not need to put cash into artificial intelligence remedies within the following fiscal year, however they must think of the access to the technology in future financial investments. Several companies do not recognize the advantages of safety and security info management as a result of commonly exhaustive economic as well as personnel prices of carrying out as well as maintaining the computer software. There's no consulting with the various other course of action. It is necessary for firms to recognize if they're getting value for cash from a security vendor. Rather, organisations can take aid of database safety and security audit services which include points like backup and also recuperation in situation of occurrences prompted by human error, natural catastrophes and also in numerous instances by cyber-attacks. Everybody in business should certainly be concerned with promoting the best standards for compliance. AppZen Audit examines data not only from the expenses but furthermore, incorporates it with countless more information sources throughout the web to discover scams as well as compliance problems that can not be matched by human auditors. An auditor should certainly be appropriately enlightened concerning the organization as well as its crucial small company activities prior to carrying out a data centre testimonial. First and foremost, he must have the skills and experience to carry out the job. For example, your cybersecurity auditors could examine a box that claims you've obtained a firewall software in place to reduce the range of websites workers can check out when utilizing firm equipment. Without the appropriate help, IT safety and security audits can be instead inefficient, along with cumbersome and also painful. Men and women who are responsible for various individuals's safety. Normally, security is a continual treatment and SelfKey will certainly proceed working closely with Uncloak to make sure that individual details continues to be as secure as possible. As mentioned by the teacher of cybersecurity school, cybersecurity has actually come to be a crucial point in all aspects. Since cybersecurity can be frustrating to have right into, take comfort in the easy fact that despite what stage your company remains in, there's something that you can do to enhance your service's cybersecurity program, starting currently. Remote gain access to should certainly be logged. Managing worker accessibility to crucial information on a continuing basis shouldn't be neglected. The system has the ability to keep track of as well as validate all activities. To observe Records, you may need to click Even more controls at the bottom. If you're certain in your operation as well as prepare to carry out reasonable modifications which make business feeling, it is mosting likely to be a welcome chance for renovation. As an example, if a CCTV operator should supply proof in court as well as it's later understood she or he's unlicensed as well as unqualified, then the case falls apart.
★
★
★
★
★
38 views • 2 slides