How an association can diminish digital abide time_
50 likes | 66 Views
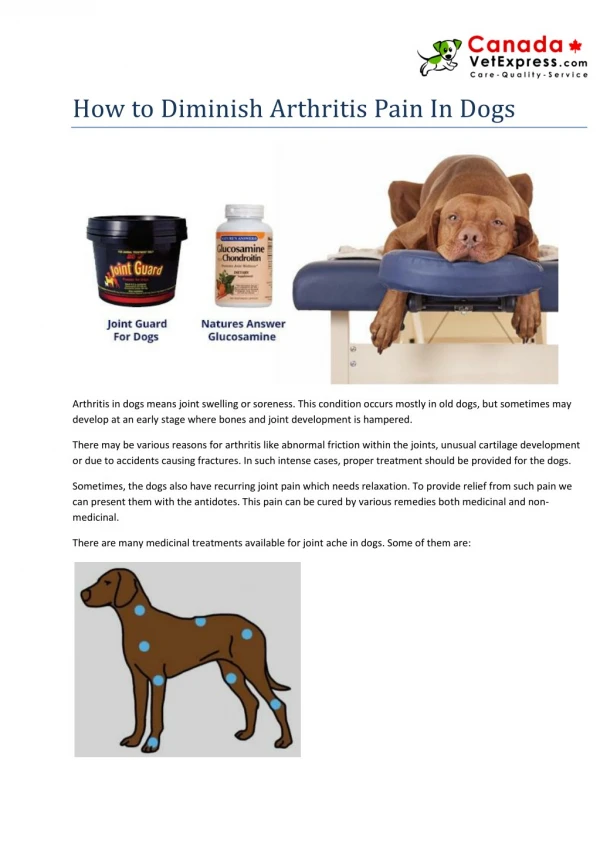
Remain time consistently augments in view of a shortfall of detectable quality on key activities. Failure to screen endpoints might allow explicit undertakings to stay away from recognizable proof. At the point when an attack has entered the environment, it can move on a level plane searching for its target. Accepting that the entry point has not been logged and seen on an anticipated reason, it might be hard to realize where the attack started. Not understanding the beginning point grows the difficulty of following which pieces of the environment have been compromised. You want Top network sa
Download Presentation 

How an association can diminish digital abide time_
An Image/Link below is provided (as is) to download presentation
Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author.
Content is provided to you AS IS for your information and personal use only.
Download presentation by click this link.
While downloading, if for some reason you are not able to download a presentation, the publisher may have deleted the file from their server.
During download, if you can't get a presentation, the file might be deleted by the publisher.
E N D
Presentation Transcript
More Related